Sambit Mohapatra, Senior Associate Consultant, Infosys and Prasenjit Sen, Senior Consultant, Infosys, in this white paper provide a framework for effective utilisation of the second line of defense (integrated assurance) for effective risk management

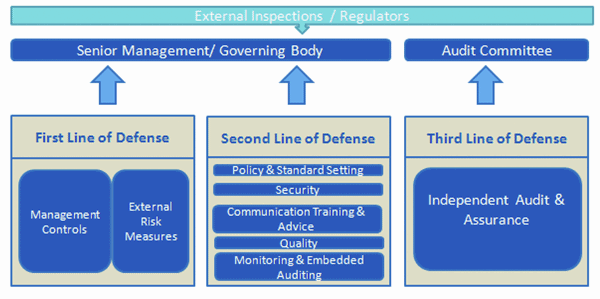
Effective Risk Management in a pharmaceutical organisation involves the strategic implementation of three lines of defense. Each line of defense provide risk governance guidance to support the ERM framework. Management control and internal sustenance forms the first line of defense in risk management, the various risk control and compliance oversight functions established by management are the second line of defense and independent assurance along with corporate audits is the third. Each of these three ‘lines’ play a distinct role within the organisation’s wider governance framework.

The purpose of this paper is to provide a framework for effective utilisation of the second line of defense (Integrated assurance) for effective risk management. It defines holistic and comprehensive audit approach of computerised systems using pharma industry’s best practices and compliance controls to demonstrate adherence to regulatory directives and guidelines. As FDA has increased focus on CSV-related inspections, CSV audits and assessments have a key role in the corporate governance structure to assure on the effective management of risk. It is not only sufficient to ensure assurance, but also to identify compliance gaps and derive insights about the compliance health. This in turn is used to strengthen the risk management controls which are the focus of this whitepaper. This whitepaper outlines our thoughts on effective audits and continuous improvements.
Business problem
Computerised systems used for supporting pharma business processes are subject to numerous regulations (like 21 CFR Part 11, EMEA Annex 11) and industry guidelines (including PIC/S, ASTM 2500 and GAMP Guidelines for computerised GxP systems).
While FDA was quiet about software and computer system validation between 2002 and 2006, this has changed significantly since 2006. Software and computer system validation has become an inspection focus for pharma, API and device industry. Deviations have been cited related to all steps of computer validation from writing specification and risk assessment to IQ/OQ/PQ, revalidation, reporting and change control. Just from 2007-2010, there have already been more than 30 such warning letters, some with disastrous consequences for inspected companies. Since 2010, FDA’s observations related to 21 CFR 11 non-compliance cover laboratories, manufacturing and clinical trials: the entire product lifecycle. The core commonality is a lack of control that calls into question the reliability of a company’s information used to make decisions around product safety and/ or efficacy (or otherwise to ensure compliance with predicate rules). Since then, the number of warning letters related to CSV have seen an upward trend. As the industry evolves, the complexity around achieving compliance has grown due to a number of factors – outsourced development and support, global infrastructure, adoption of cloud, to name a few.
Looking at Indian context, FDA has issued warning letters to atleast five Indian firms in 2016 and four out of them had some form of violations related to computerised system. It is evident that almost 80 per cent of the warning letters related to computerised systems. Clearly, it is high time for all small and large Indian pharma firms to put proper processes in place if not already done.
In response, most pharma sponsors have put in place robust IT risk management controls and procedures. The efforts to strengthen the first line of defense have matured in line with regulatory and industry guidance. From a regulatory compliance perspective, it is more pivotal to strengthen the second line of defense which can proactively identify issues.
The second line of defense is implemented with internal quality assurance audits and periodic review procedures. However, in IT divisions of many pharma companies, there is a lack of integration between these processes. Thus the related information is not being leveraged to gain valuable insight that drives more rapid improvements in processes, solutions and compliance.
Often audits are performed by multiple teams based on their area of responsibility with inadequate coordination and consolidation of findings. Audit and review has intended to be driven from a desire to achieve and demonstrate compliance with regulatory requirements, rather than to find actual gaps, continuously improve and achieve greater efficiency in the operation of systems. Here lies the potential for significant value addition in deriving insights for process improvement and maturity by analyzing the audit observations and periodic review findings and having a feedback process which is integrated, comprehensive and aligned to the process control effectiveness.
Regulatory requirement for defining audit approach
Before defining the audit approach, there needs to be a clear understanding of the audit requirements as mandated by regulatory guidelines. Most of the audit requirements are derived from GxP, SOx and privacy regulations like the ones mentioned below:
- GxP requirements: GxP is based on guidelines for the pharma industry and covers all steps from drug development to production. It is enforced by industry regulations such as 21 CFR Part 11 and predicate rules, EMEA Annex 11, 21 CFR Part 820, IEC 62304 & 60601 and ISO 14971 & 13485.
- SOX Section 404 (Sarbanes-Oxley Act Section 404) Controls: This mandates that all publicly-traded companies must establish internal controls and procedures for financial reporting and must document, test and maintain those controls and procedures to ensure their effectiveness.
Major IT SOx focus areas are:
- Management of change including development projects
- Management of change includ User access management to application, database and operating system, and finally
- Management of change includ Computer operations and configuration management
The operational GxP audits include change and configuration management, incident management, security management including data integrity checks, back up, restore and business continuity.
Computer operations sox audits consists of back up and monitoring controls.
Infosys solution framework
The integrated risk management solution approach provides high focus on the second line of defense. An integrated and comprehensive audit framework not only provides a high degree of assurance but also provides a detailed feedback to strengthen the first and second line of defense.
The second line of defense encompasses both monthly audits and yearly periodic reviews. The monthly audit involves assessment of a specific operational process area for planned applications while the periodic review covers all process areas for the respective applications. The audit process starts with defining a risk-based audit approach with inputs from all the stakeholders including process owners, system owners, service managers, BAU teams, Site IT Lead. Based on that an audit plan and periodic review plan are prepared which are streamlined at the planning level.
Audit and periodic review are conducted as planned based on a comprehensive checklist as per applicable GxP good practices, sox controls and internal guidelines. The observations and suggested corrective and preventive actions are then published in audit reports. While the corrective and preventive actions are tracked to closure, the audit and periodic review observations are used to prepare a live dashboard with compliance health information for all critical and regulated applications. The observations are also used as an input for preparing the consolidated audit analysis report. Based on the analysis, gaps are identified which are remediated using continuous improvement plans. The process gaps are also taken as inputs for design effectiveness reviews. Any new control/ process established as part of the improvement process is checked for proper implementation during next audit cycle.
Detailed audit framework
Audit approach: The starting point for the framework is definition of an audit approach. The audit approach defines the scope and level of audit required based on risk assessment and projected benefits. This is defined based on risk assessment and feedback from IT Strategy and Continuous improvement plans. This defines the overall scope and objectives of the audits.
This is aligned with the overall IT strategy and takes feedback/ input from audit analysis of previous year. It forms the basis for audit requirement defined in the audit plan. For e.g., if there are many audit observations in the change management process, it may need more frequency of change management audits.

Furthermore, the input of all stakeholders (including functional process managers, quality process leads, system owners, service managers, BAU teams, Site IT Lead etc is taken at this phase. This is essential to understand the audit needs based on future plans like migration, upgrade, infra migration or other major changes and activities that may affect the compliance status.
The audit is conducted based on a comprehensive checklist as per applicable GxP processes and SOx controls. The checklist is customized based on internal guidelines of the pharma company. It is periodically updated based on feedback from the audit analysis. The update also covers any new processes/ controls established as part of continuous improvement plans.
Audit and periodic review planning: Audit planning and periodic review assessment tracker follows the audit approach. Proper planning for each category of audit is essential to ensure smooth conduct of audit. This includes defining which processes/ sub – processes is audited, defining the timelines, schedule, specifying the auditors, determining the resource requirements from audited team.

The audit plan and the periodic review assessment tracker are streamlined at the planning level. This alignment ensures that no application/ process combination is audited twice. If a process for a particular application is audited as per plan, the same is taken as an input for the periodic review assessment. If a periodic review assessment of last year requires a follow up audit for verifying remediation action that is incorporated in next year’s audit plan.
Audit and review process: Based on the audit plan and periodic review tracker, audit and periodic review is conducted and observations are noted in audit report. Proper CAPA is suggested for remediation.

At this phase, some audit findings are taken as an input for the periodic review. As audits are conducted monthly, they can be easily taken as input for the yearly periodic reviews. For e.g. if an audit of change management controls for application is done in February, the same can be used as input for the periodic review of the application. There is no need to conduct change audit again during the periodic review.
The observations also go directly into the live compliance dashboards which displays the compliance health of each application. The dashboards have multiple filters to view the compliance status for each application or each process area.

Analysis: Rather than limiting the audit process with remediation actions, analysis of the audit observations and of the periodic review observations is done. The includes observations across all IT audits conducted in the organisations. The audit analysis is based on audit reports for the audit period which provides insights for QMS areas across all applications. The periodic review analysis includes application specific analysis. There can be gaps or deviations specific to the particular application teams in terms of lack of process or technical knowledge.
Analysis report and insights: Based on the analysis, a consolidated analysis report is prepared. The report also incorporates an analysis of compliance incidents, process gaps and deviations. It has the details on process, knowledge and technical gaps.
- Process gap: The audit analysis identifies gaps specific to any QMS process.
- Knowledge gap: There can be process specific knowledge gap across the organisation or specific to a particular application team. Analysis of yearly audit observations identifies the organisation wide knowledge gap and analysis of periodic review observations identifies application specific gaps.
- Technical gap: Identification of technical gap is very essential as technical issues in regulated systems cause a corresponding compliance impact.
- Continuous improvement: Based on the insights, a comprehensive continuous improvement plan is prepared. All the process related gaps are first used as an input for design effectiveness review (DER). The DER entails review of all applicable control to verify if the existing controls are sufficient for a compliant QMS process. Identified gaps may require establishing new controls and thus the update of SOP’s and guidelines. Any required updates for Sop’s/ guidelines forms a part of the CIP. Similarly, the CIP plan includes conducting training sessions to address identified knowledge gap and Technical automation/ bug fix to address any technical gaps.
Case study
A top pharma company wanted to streamline its audit and review process and somehow integrated that with the continuous improvement process. We started with defining an audit approach based on discussion with all the stakeholders and then the audit plan. Audit and review were conducted as per the plan and at the end of audit period, the observations were analysed to derive insights and integrate that into the continuous improvement programmes.
The numbers and percentage below are only indicative. The audit finding are also indicative and do not directly correlate to any particular firm.

Industry benefits
This framework offers a full proof approach for pharma firms and especially can be used as guidance by Indian pharma companies to streamline their process to meet global regulatory requirements. As a leading IT vendor with global experience, this is an attempt by Infosys to help the promising Indian pharma industry to cope with changing regulatory framework challenges. It offers the following key benefits:
- Integrated audit approach: The framework covers all the audit processes as required by regulatory guidelines. Furthermore, the entire framework is handled by a dedicated team of audit champions who have an extensive overview of the compliance health of the entire organisation and can take informed decisions on audit requirements and control frameworks.
- Extensive compliance monitoring and external inspection preparedness: The integrated audit approach comprehensively monitors and evaluates the effectiveness of internal controls and risk management which in turn also helps to identify and mitigate non-compliance and potential risks to ensure preparedness for external inspections.
- Consolidated audit analysis and insights: Consolidated insights, analysis and trend reports for senior management to track compliance health
- Comprehensive continuous improvement: Based on the insights, comprehensive continuous improvement plan is prepared to reduce the compliance incidents/ deviations/ process gaps to zero by executing a series of targeted systematic improvement plans
References:
1. http://www.rsc.org/events/detail/4529/learning-from-
recent-fda-warning-letters-related-to-computer-validation-and-part-11-prepare-yourself-for-the-upcoming-fda-part-11-
inspections-webinar-by-globalcompliancepanel
2. http://ceruleanllc.com/wp-content/articles/CERULEAN_FDA_21cfr11_Enforcement_ContractPharma092011.pdf
3. http://www.labcompliance.com/solutions/expert_advice/ computers/4103-warning-letters-csv.aspx
Views expressed by the authors are personal
- Advertisement -


Comments are closed.